Cybercrime in the wake of COVID-19

The COVID-19 pandemic has not only triggered a global healthcare crisis, but it has also disrupted societies in unprecedented ways. A slew of lockdowns and restrictions on the freedom of movement have forced us to revisit the way we work and live.
To that end, the internet has played a critical role in maintaining a semblance of normality by connecting people and businesses. But it has led to a spike in cybercrime and attacks as well. Criminals are using new tactics that are rising steadily in volume and sophistication.
Gerald Reddig, who leads Nokia’s portfolio marketing for security and network management solutions, in an interview, warned that the chances of falling victim to scams and fraud are considerably higher now.
- COVID-19 seems to have triggered a spike in cybercrime? In your assessment how serious is the issue?
In February and March, the monthly mobile infection rate rose by almost 30 percent compared with the previous months. The reason for the increase is the significant escalation in cyber security incidents related to COVID-19.
As the world prepared and addressed the coronavirus menace, shifting to accommodate shelter-in-place and work from home mandates, new threats arose in our networks. In the recent months, security teams have witnessed a dramatic uptick in the number of scams, such as phishing campaigns that use fake emails to steal private credit card information and credentials.

- What kind of tactics are cyber criminals employing to carry out attacks?
Post-mortem analysis of data breaches shows that most of today’s cyberattacks are frontended by phishing campaigns.
This is not surprising, since the easiest way for a threat actor to gain access to sensitive data is by compromising an end user’s identity and credentials. Things get even worse if a stolen identity belongs to a privileged user, who has even broader access, and therefore provides the intruder with “the keys to the kingdom”.
While paying close attention to established hackers’ tactics, techniques, and procedures (TTPs) increases an organization’s ability to implement effective cyber defense strategies, businesses need to stay abreast of emerging TTPs as well. A good example is a TRUST umbrella to strengthen security postures.
Organizations, CSPs in particular, can bolster resilience by aligning their cyber defense strategy based on threat actors’ TTPs. However, as the emergence of vishing - a form of phishing - illustrates, organizations need to adapt their strategies in response to changes in their adversaries’ TTPs.
- We discuss a lot about how individuals are vulnerable to phishing and malware. What about SMEs and large enterprises?
Teams led by the chief information security officer (CISO) must look for a security orchestration and response architecture that integrates AI and automation to aggregate and analyze data from a variety of network and system sources. These include security information and event management (SIEM) solutions, firewalls, endpoint detection and response (EDR) tools, ticketing systems and other critical security technologies — saving hundreds of hours in manual effort.
By adopting these capabilities, enterprises will set themselves up for longer-term 5G success. Automation and AI will be essential to capitalizing on 5G opportunities in new vertical markets and assuring end-to-end quality across a diverse range of use cases and business models.
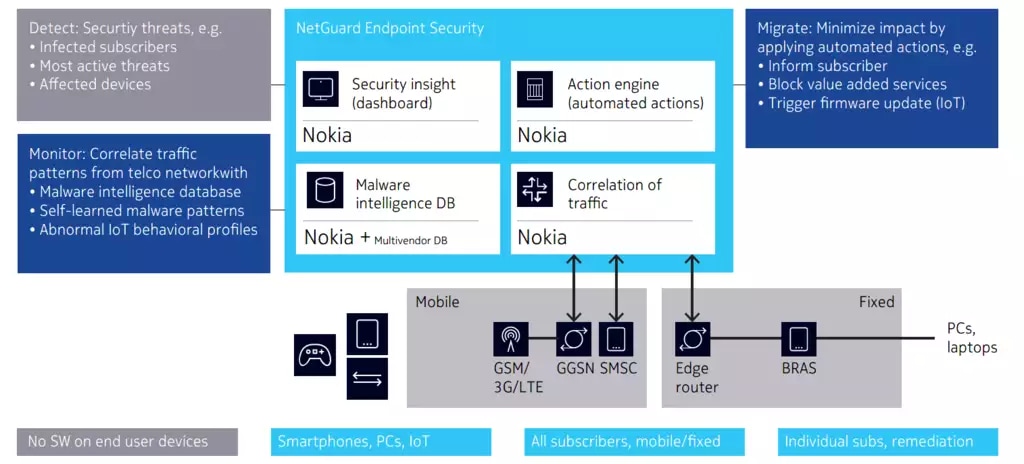
- How does Nokia’s NetGuard Endpoint Security help in this regard?
The NetGuard Endpoint Security (NES) solution is a network-based malware detection solution that enables customers to monitor their fixed and mobile networks for evidence of malware infections in consumer and enterprise endpoint devices, including mobile phones, laptops, personal computers, notepads and the new generation of Internet of Things (IoT) devices. The solution is deployed in major fixed and mobile networks around the world, monitoring network traffic from more than 150 million devices.
How can 5G help boost network integrity?
The innovation applied to secure the networks we operate today in visibility, segmentation and mitigation controls builds on previous success, making the threat surface of 5G more manageable by applying techniques such as automation, orchestration, distributed network build and operation, policy and analytics. Early and integrated threat detection is key. Detection needs to go beyond signature-based tools to spot the attacks designed to evade basic filters. Behavior-based checks on endpoints are important. Combinations of packet capture, big data and machine learning (ML) can be used to identify threats not spotted by basic filters. Finally, security solutions cannot be limited to addressing specific communication modes serving only their niche ecosystems as they do today. 5G security needs to be both comprehensive and embedded into the design, not appended as a separate mechanism.
- What would be your recommendations to users at a time when the reliance on communications technology has increased manifold?
The individual user needs to be careful and vigilant when browsing websites or opening email attachments. The most important aspects to consider are:
• Visit websites that are known to be reliable sources of information on the pandemic
• Only install applications from trusted app stores (Google Play, Apple, Microsoft)
• Use an up-to-date anti-virus program on the mobile device
• Keep applications and operating systems running at the current released patch level
• Do not open email attachments from an unknown sender and if it’s unexpected
• Desist from granting additional execution privileges if there is no clear reason and need to do so
Learn more:
About Nokia
We create the technology to connect the world. Only Nokia offers a comprehensive portfolio of network equipment, software, services and licensing opportunities across the globe. With our commitment to innovation, driven by the award-winning Nokia Bell Labs, we are a leader in the development and deployment of 5G networks.
Our communications service provider customers support more than 6.4 billion subscriptions with our radio networks, and our enterprise customers have deployed over 1,300 industrial networks worldwide. Adhering to the highest ethical standards, we transform how people live, work and communicate. For our latest updates, please visit us online www.nokia.com and follow us on Twitter @nokia.
Media Inquiries:
Nokia
Communications
Phone: +358 10 448 4900
Email: press.services@nokia.com