As hackers evolve, so does our defense: Securing 5G with AI

Cyberattacks on critical infrastructure are becoming more targeted, stealthier and harder to detect. They exploit vulnerabilities over time, blending into the normal flow of operations. For example, Salt Typhoon recently infiltrated telecom infrastructure across North America, maintaining long-term access to steal data. In Europe, Sandworm has just shifted its tactics, using precision spear-phishing campaigns to infiltrate the energy sector before deploying destructive malware.
As these threats evolve, defense strategies are also shifting from reactive measures to prevention. With the expansion of 5G networks, cybercriminals now have even more avenues to exploit vulnerabilities and more places to hide. Staying ahead means anticipating attackers' moves, identifying the patterns they leave behind, and neutralizing threats before they can cause damage.
AI in telecom XDR: Adapting at the speed of threats
5G networks generate vast amounts of security data that is too much for traditional tools and human analysts to handle efficiently. That’s where AI and Extended Detection and Response (XDR) systems make a difference. XDR integrates data from endpoints, cloud environments, and security systems to deliver a unified view of telecom networks. AI then analyzes this data, spotting anomalies and uncovering hidden patterns at machine speed.
With the billions of data points generated by 5G’s scale and complexity, Large Language Models (LLMs) are well-suited to analyze and interpret this information. When combined with XDR, LLMs can reduce detection and resolution times from hours to minutes, depending on the nature of the cyberattack. For example, the GenAI assistant in NetGuard Cybersecurity Dome, powered by Microsoft Azure OpenAI GPT, demonstrates how LLMs can enhance threat analysis and improve decision-making during a cyberattack.
The shift to proactive threat hunting
Ponemon Institute reports that the average time to detect and contain a breach is 258 days. Bridging this gap requires proactive measures: actively hunting for threats with telecom-specific intelligence, real-time monitoring, and predictive analytics. This involves assessing vulnerabilities within a business and technical context and prioritizing those that pose the greatest risk.
AI tools like the Hunt Assistant help security data scientists by analyzing external threat intelligence and telemetry data to identify suspicious patterns, integrating with MITRE models for tactics, techniques and procedures (TTP) monitoring, and generating new mitigation use cases for human review. These tools create a feedback loop with LLM-based AI assistants used by SOC analysts, transforming threat intelligence into actionable security measures. This collaboration ensures that no threat, no matter how hidden, slips through the cracks.
Nokia is telecoms’ XDR choice. What’s yours?
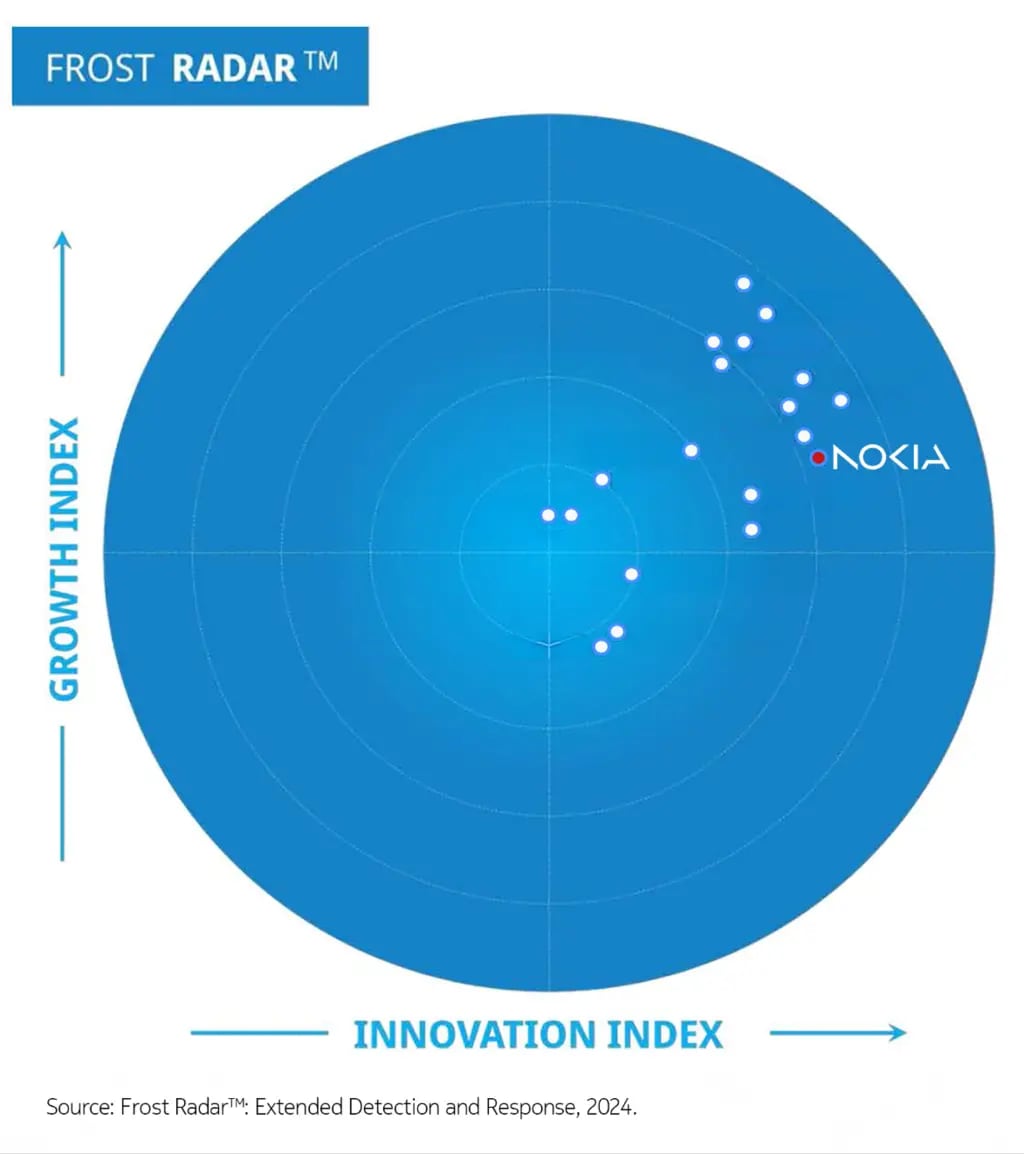
Nokia’s recognition in Frost & Sullivan’s Radar Report as #2 innovation leader in XDR reflects our commitment to continuously increase the cyber resilience of critical network infrastructures. Our XDR solution delivers deep visibility and observability across RAN, transport, and core domains.
“Nokia has a unique position in the market as the vendor of choice for telecommunications enterprises, thanks to its comprehensive coverage of telco and OT environments, strong know-how of the industry, connections to the market, and technology capabilities” – notes Lucas Ferreyra in the radar report.
Nokia XDR integrates proactive tools like AI-driven threat hunting, real-time threat intelligence and tailored 5G security use cases and playbooks to help operators secure their networks today while preparing for tomorrow.
Control the game
Telecommunications are under pressure to achieve five-nines availability, which means a maximum 5.26 minutes of downtime per year. Their security must go beyond reacting to attacks; it must anticipate and prevent them before they occur. With new government regulations tightening around critical infrastructure, telecoms can no longer afford to wait for the next attack to hit.
The game of hide-and-seek between attackers and defenders may never end, but with proactive and intelligent tools, telecom operators can ensure one thing: attackers will always be on the losing side.




