Simpler and more secure access for private wireless networks

Asset-intensive enterprises are deploying private wireless networks based on 4.9G/LTE and 5G technologies to bring Industry 4.0 digitalization to their operational technology (OT). But the complex nature of OT environments means that they may find it challenging to manage the accounts of operations staff responsible for different areas that can access and administer these networks while keeping them secured. Enterprises need simple, flexible, and secure approaches to identity and access management (IAM) to get the most from private wireless and unifying with organization’s IAM, can bring strong benefits.
For example, an enterprise that has deployed private wireless networks at several facilities may use a network management system (NMS) that has its own dedicated user accounts. The access rights for these accounts could be determined by role-based access (RBAC) policies that vary from facility to facility.
As a result, the enterprise and its partners will likely need to manage multiple sets of user credentials as well as to cope with the RBAC model’s inflexible rights-granting rules. A user that is responsible for managing the private wireless networks at multiple sites in different roles may require several accounts. This leads to operational efficiency and increased security risk in the form of an expanded attack surface.
Federated identity management and attribute-based access control
The ideal scenario is a federated identity management approach leveraging single sign-on (SSO) that allows members of the network operations team to have one set of authentication credentials that applies to all private wireless network assets. These credentials should be the same as those they use to access the enterprise’s IT systems. In this way the user authentication is delegated to an external, trusted identity provider to avoid siloed authentication for the various systems in the IT and OT environments.
Authorization of the private wireless OAM users should be based on the more flexible attribute-based access control (ABAC) method instead of the rigid RBAC model. ABAC brings greater granularity to user authorization because it allows enterprises to assign access rights for private wireless network management functions and API’s based on user roles and other object and environmental attributes. For example, an OAM user that has been authenticated through SSO can have administrator rights for the private wireless network in one facility but only view rights for the network in the other.
Solutions that combine SSO and ABAC in the IAM process for private wireless networks can enable enterprises to:
- Strengthen their security posture by defining access permissions in a more granular way, by creating unified user credentials stored in a trusted place
- Increase their operational efficiency through simpler user account management by enabling private wireless OAM users to access all IT and OT systems with one account.
- Take greater control over which users, partners and customers can access their networks
Two ways to access Nokia DAC
Nokia Digital Automation Cloud (DAC) is a cloud-managed edge-centric private wireless solution that uses SSO and ABAC to provide two main IAM options for administrative users. Azure AD is natively supported while other existing IAM systems like Keycloak or Google can also be integrated leveraging Security Assertion Markup Language (SAML) protocol.
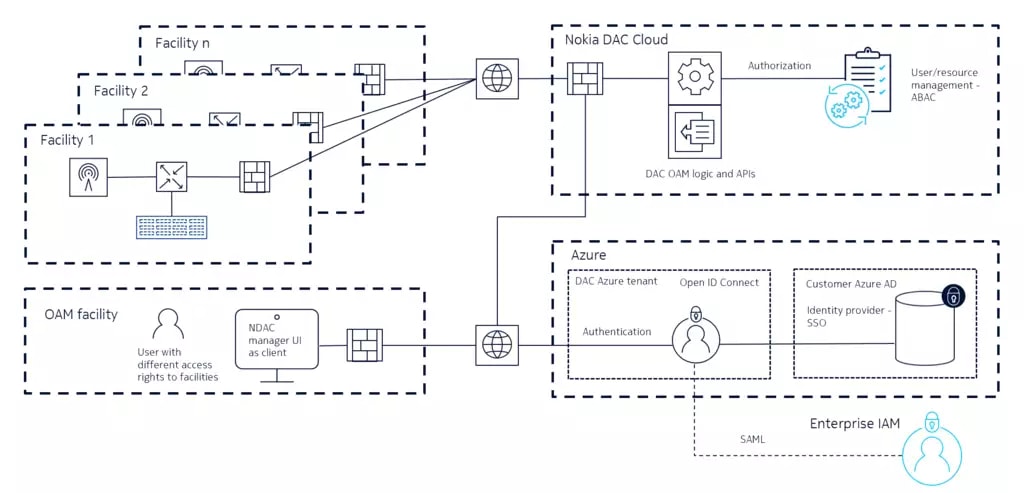
Accessing Nokia DAC with SSO and ABAC
Find out more
Nokia DAC provides flexible and simplified IAM approaches that can simultaneously help you reduce your attack surface and increase operational efficiency of your private wireless networks to power Industry 4.0 use cases. Visit our website to find out more about how Nokia DAC can provide the industrial-grade connectivity and automation you need to ensure a fast and successful digital transformation.




