The compromised insider attack challenge – how to detect and respond before they cause harm

5G technology has been a game-changer in the world of telecommunications. It promises to provide faster speeds, lower latency, and more reliable connections. However, with this increased capability comes a greater need for security. In order to ensure that 5G networks are secure, it is important to understand the risks and how to mitigate them.
Nokia is a leader in the 5G networks industry, providing innovative solutions for the secure and efficient communication of information. With the rise of cyber threats and attacks, it is more important than ever to ensure that networks and systems are protected. One area of concern is insider attacks, where a trusted insider misuses their access to cause harm to the organization.
In this article, I will explore the role of XDR (extended detection and response) in detecting and responding to compromised insider attacks.
Challenge
One of the biggest challenges facing businesses today is the threat of compromised insider attacks, where an employee or third-party contractor with access to sensitive data intentionally or unintentionally exposes the organization to cyber risks.
In 2022 the Cost of Insider Threat report conducted by Ponemon Institute said: “Insider threats have increased in both frequency and cost over the past two years. Credential thefts, have almost doubled in number since last 24 month. The time to contain an insider threat incident increased from 77 days to 85 days.
To prevent and detect these types of attacks, organizations need to implement a comprehensive security strategy that includes a combination of non-technical and technical measures. Non-technical measures, such as security awareness training, background checks, and regular audits, help organizations build a culture of security and mitigate the risk of compromise. Technical measures, such as access controls, data encryption, and threat detection and response solutions, help organizations prevent and detect malicious insider activity.
Innovative solution
Communication Service Providers need to adopt a multi-layered security approach that includes XDR or eXtended Detection, and Response solutions.
XDR solutions use artificial intelligence (AI) and machine learning algorithms to analyze and identify potential security threats. This enables CSPs to detect and respond to security incidents in real-time, providing faster and more effective protection against cyber threats.
One of the key benefits of XDR is its ability to detect and respond to compromised insider attacks. XDR solutions monitor the behavior of insiders, including the systems they access and the data they use, and can identify any unusual or malicious activity. For example, if an insider is accessing sensitive data that they should not be, XDR can alert the security team and block the access, preventing the data from being stolen. XDR can also monitor the activities of insiders on remote devices, such as laptops and smartphones, providing protection against remote insider attacks.
XDR is a cutting-edge security solution that provides organizations with the necessary information to also respond effectively. XDR solutions collect and analyze data from multiple sources, including endpoints, networks, and SIEM, to provide a comprehensive view of the attack. This information can be used to determine the scope of the attack and the data that has been compromised, enabling organizations to respond quickly and effectively.
AI and automation bring down the cost of a breach
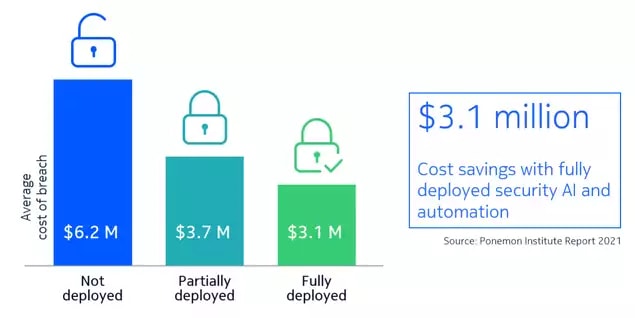
In addition to improving security efficiency in detection and response SaaS-based XDR also helps CSPs to increase flexibility in scale and to reduce costs. By centralizing security management and automating many security processes, security operations team can reduce the need for manual intervention.
Summary
These innovative security technologies allow a CSP security operations team to simplify incident risk management, reduce the 5G attack surface, and respond more effectively to security threats such as compromised insider attacks.
At Nokia, we understand the importance of protecting a critical infrastructure from cyber threats. Our telco-centric XDR, detection, and response solutions are designed to provide a comprehensive view of your security posture and help you respond to cyber threats quickly and effectively. Read here more about XDR – Choosing the right solution for your modern security operations.
Nokia XDR portfolio for 5G Security
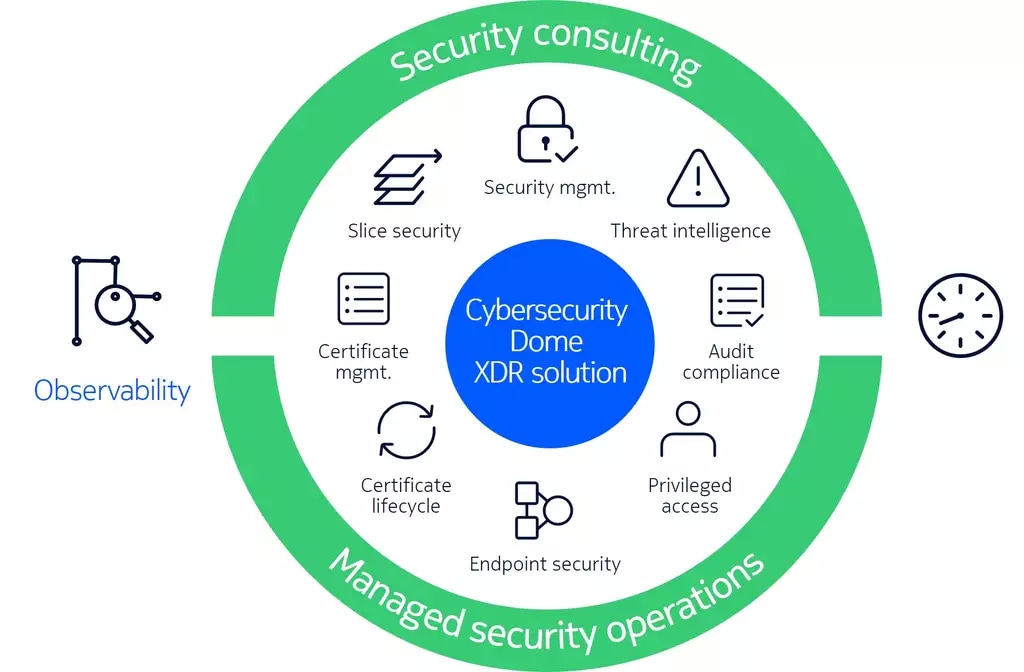
Connect with our 5G security experts to learn more about how we can help you protect your enterprise from cyber risks.
Additional resources:





