Trust thy 6G network: The future of communications hinges on security and privacy

In the 6G era we will need to put far more trust in the network than we do today. In the 2030s, we will immerse ourselves in new digital worlds, utilizing holographic telepresence to brainstorm with our colleagues and experience intimate moments with our families halfway across a city – or even across the world. We will have a wealth of robots at our disposal. Highly orchestrated multi-robot systems will revolutionize industry, but collaborative robots will also spread to everyday life, for instance helping to care for the elderly or the infirm at their homes. Augmented intelligence in conjunction with body-area networks will monitor our biochemistry, warning us of potential health problems long before we experience symptoms.
These disparate scenarios have two things in common. First, they will be fueled by 6G networks. Second, all these use cases will require new levels of security, cyber-resilience, privacy and trust. We will need to know that our extended reality meetings and conversations are private, that our robot systems are secure and that our most personal health data is protected.
Solving and proactively tackling the challenge of security, privacy and trust will be key unlocking the full value potential of 6G-era communications. At the same time, the threat of malicious attacks will expand due to the proliferation of billions of devices and sensors and millions of subnetworks that typically reside in untrusted domains. As our networks evolve for the future, aspects of that transformation will contribute to growth of that threat vector in multiple dimensions, for instance through open interfaces and architectural disaggregation, the mingling of open-source and multivendor software, and multi-stakeholder supply chains. Moreover, in the 2030s artificial intelligence and machine learning will play a much larger role, for good and bad. While AI/ML will benefit 6G security immensely, we’re also likely to see many AI-initiated attacks as well as attacks directed against the vulnerabilities of AI/ML-based mechanisms in our networks.
What we need is a comprehensive set of security technology enablers for the 6G era, enhanced and supported by AI/ML and new principles of cyber-resilience. We require a new paradigm for the way we create software. Software generation will need to become fully automated. Those automation tools will include static and dynamic bug detection, code optimization and automated code testing. Experimental and continuous in-production fault injection for testing purposes will likely become the norm, assuring cyber-resilience in the 6G era. And just as important, automated, distributed, cognitive closed-loop security operations need to be part of our 6G security vision.
Nokia Bell Labs has just published a new white paper exploring the new security, privacy and trust requirements for the 6G era. We will explore some of these specific security priorities below.
Privacy will become paramount
In the 6G era, the network and its services will continuously generate, store and process massive amounts of data. Digital breaches in the 2030s could expose far more than credit card numbers and confidential business messages. As the 6G network becomes our digital sixth sense, it will become capable of determining a person’s precise position within a room, as well as tracking and predicting their habits. As 6G biosensing emerges, the network may know our most intimate health details in order to monitor our medical conditions and medication levels or even warn us of an imminent heart attack or epileptic seizure. However, this data could be used for increasingly sophisticated fraud, blackmail and extortion attempts. It could be used by unscrupulous businesses to target potential customers based on their most intimate preferences and fears. And it could be used by governments to monitor its citizens.
Similarly, the confidentiality of business data will assume even greater importance. Many business cases today are founded on the controlled access to and ownership of customer, process and business data, and those cases will become the norm. This opens businesses up to ransomware attacks by denying access to data or for corporate espionage. “Deep fakes” in the virtual world of the 2030s will pose tremendous challenge and risk.
So how can we reap the benefits of advanced health monitoring without falling victim to malicious data appropriation? How can we fully digitalize our businesses without opening ourselves to relentless attacks? We will need anonymization and privacy-preserving technologies that strike a balance between minimal data exposure and legitimate analytics.
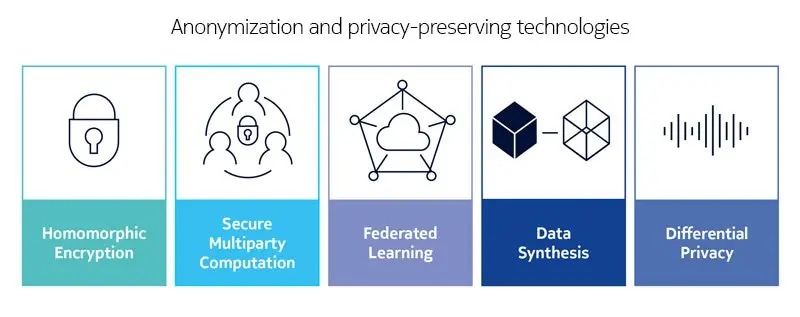
Those technologies will include homomorphic encryption, which permits us to analyze encrypted data while yielding the same encrypted results as if the analysis were conducted on plain data. They will include secure multi-party computation that doesn’t disclose internal data. They will include distributed storage and processing at edge and central data centers along with federated learning approaches. We will also need to develop techniques that transform raw data into a form of synthetic data that maintains characteristics necessary for analytics but discards or secures characteristics that are irrelevant or private. All of these will be built on technologies that attest data integrity, provenance and ownership. Trust technologies like Trusted Platform Module and Trusted Execution Environments will protect data integrity and provide proof of data ownership anchored in silicon and hardware. Blockchain technology will continue to support distributed data brokerage by securely tracking data access rights.
The need for quantum safe security
The emergence of quantum computing and quantum communications will have profound implications for security technologies and cyber-resilience. By applying principles of quantum physics, we are creating computers with unparalleled capabilities and communications channels with unbreakable encryption. But the same applies in reverse. Those same technologies can be used to compromise security measures once thought impenetrable.
While the underlying mechanisms of quantum physics in the context of quantum communications are well understood, there remain fundamental challenges to the practical implementations of quantum switches, routers and error-correction technologies when building computing infrastructure at scale. However, we must start preparing for a quantum-computing future now.
Today’s asymmetric cryptographic algorithms will likely need to be replaced with quantum-safe concepts. And in the case of sensitive data of long-term relevance such replacement needs to be tackled now so we can protect today’s data stored on servers against future quantum-compute-based algorithms. Novel quantum algorithms such as Quantum Key Distribution may provide a new approach to secure 6G networks and protocols. Meanwhile, quantum safe cryptographic schemes such as lattice-based or code-based approaches are currently showing much promise.
Defending the factory floor
Campus and localized specialized networks will become the norm in the 6G era, and those networks will increasingly become targets of security attacks. Jamming a private network could bring a factory operation to screaming halt. Or worse, the high level of automation in future factories could lead to more sophisticated types of industrial sabotage. Rather than just shutting down a network, an attacker could attempt to take over the robots and machines connected to it, creating chaos on the factory floor, costing millions due to lost production time and even causing damage or injury to the people working on it.
6G era industrial security measures must be able to mitigate these attacks with technologies such as jamming detectors, directional null steering for uplink jamming mitigation and frequency hopping.

Security, privacy and trust are must-have technologies of the 6G era, but they are far from the only ones. Nokia Bell Labs is researching multiple technologies that we believe will define the 6G networks of the future: new spectrum technologies above 100GHz, the joint design of networks for both communications and sensing, AI/ML-defined air-interface frameworks and novel architectural concepts such as cloud-capability discovery and end-to-end service management across what will be fully distributed and heterogeneous cloud environments. We cover all of these concepts in the white paper “Communications in the 6G era,” but we are exploring each in detail in the Bell Labs blog and in separate papers.
Without security, privacy and trust, the 6G era would be moot. 6G will bring amazing new capabilities to the network and enable countless new applications that will help the world act together. But unless consumers, businesses and industries are comfortable that those networks and applications are secure, private and trustworthy, they will never embrace them.
The full security white paper is available for download here.

