How to overcome challenges with botnet DDoS detection

In our previous blog post, The rise of botnet DDoS, we shared results from our “DDoS in 2021” report covering broad trends in Distributed Denial of Service (DDoS) over the last two years.
One of our major recent findings was that most DDoS today comes from botnets, including most of the recent publicly reported terabit-level attacks. The dominance of botnets represents a major shift from 2021, when our research showed most DDoS traffic originated in a small number (< 50) of “bulletproof” hosting providers and “booters” (websites specialized in “DDoS services for hire).
While botnets are responsible for some of the largest high-bandwidth and high packet-intensity DDoS attacks (volumetric attacks) today, botnets also generate the majority of application-level attacks. Today, botnets pose the fastest growing and most significant DDoS threat to service providers and data center networks. This is illustrated in figure 1, which shows the comparison in daily aggregate DDoS volumes between DNS amplification and botnet-driven DDoS between February 9 and March 12, 2022.
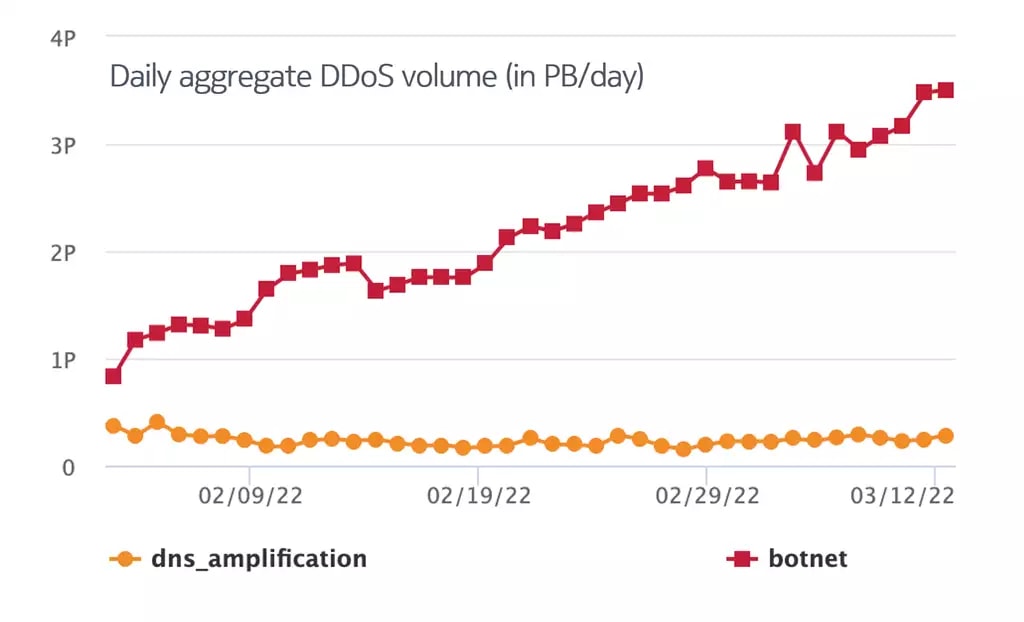
Figure 1. Comparison of aggregate volume levels for DNS amplification and botnet DDoS attacks in February-March 2022 (source: Nokia Deepfield, data from collaborative work with North American Tier-1 service providers)
What makes detection of botnet DDoS traffic more challenging?
The challenge for earlier generations of DDoS protection approaches (such as scrubbing centers or scrubbers) using payload-based machine learning (ML) is that ML requires meaningful features for extraction. These systems rely on distinguishable IP header or payload characteristics to declare network flows as DDoS.
However, these distinguishable features are not present in most of the latest large-scale botnet DDoS attacks we see today.
For example, here’s a Wireshark screenshot from an HTTP-Burst attack. Note that the request for a top-level page (i.e., “/”), user-agent, HTTP options, etc. are all perfectly valid and match legitimate web requests. The HTTPS PCAP sample used for this analysis includes several million packets from many thousand botnet devices – all with valid TCP/IP headers, statistically representative user-agents, and valid form requests matching those made by legitimate traffic to the victim website.
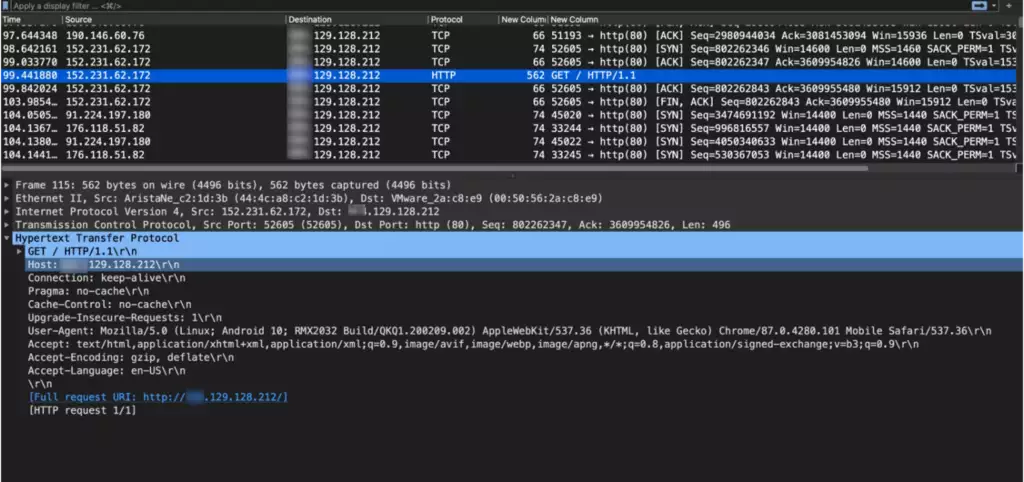
Figure 2. A snapshot from the Wireshark tracing tool of a botnet DDoS attack
In other words, this sample has no meaningful payload or IP header features to distinguish it from legitimate network traffic.
So, given the massive rise in botnets and the increasing ability of botnets to generate realistic application payloads, how can a network operator block the new generation of botnet DDoS?
Tracking the history of botnet DDoS attacks
Our research uncovered more than 250,000 compromised IP endpoints used in botnet DDoS on an average day worldwide. These botnet IPs include a broad range of compromised cloud servers, enterprise VoIP phones, poorly secured enterprise servers, and many thousands of web cameras and digital video recorders. Multiple groups of commercial hackers and booter websites conscript these compromised IPs into dozens or hundreds of DDoS campaigns each day. These commercial DDoS campaigns extort money from enterprises, attack government infrastructure, and disrupt Internet service for a broad range of other illicit goals.
Over the last two years, Nokia has compiled one of the largest libraries of real-world DDoS attacks in the industry. Our Deepfield DDoS Library (DDL) includes thousands of geographically, topologically, and commercially diverse attacks using every known DDoS vector, including amplification/reflection, flooding, and botnet/application. The DDL includes samples from all operational commercial booters and hundreds of anonymized daily samples from collaborating network operators. DDoS samples in our DDoS library range from low-volume HTTPS application-level attacks to the multi-terabit botnet and amplification floods.
Many of the captured attacks encompass dozens or hundreds of variations, including combinations of TCP flag variations, minor differences in payload content, etc. Industry and hackers often give these attacks a variety of different names. For example, the darknet booter-based market has terms like “XSyn,” “Dominate,” “BlueSyn,” “TCP-Bypass,” “TCP-Doom,” “Green-Syn,” and many other exotic appellations. All of these are just different names for basic TCP SYN floods.
Understanding the larger internet security context
Automated security and machine learning require massive, frequently updated data sets. Nokia combines daily updates to DDL with global scale tracking of IP endpoints and botnets. Leveraging more than a decade of research and development, Nokia’s patented Cloud Genome hourly crawls the entire active internet address space (3-4 billion IPv4 and IPv6 addresses), identifying both commercial services as well as millions of IoT devices, security vulnerabilities and other threats.
For example, Figure 2 below shows how Deepfield Secure Genome helps identify several hundred compromised servers in a specific service provider’s network. These servers participate in dozens of attacks each day against consumers and businesses across the internet (and, occasionally, other customers).
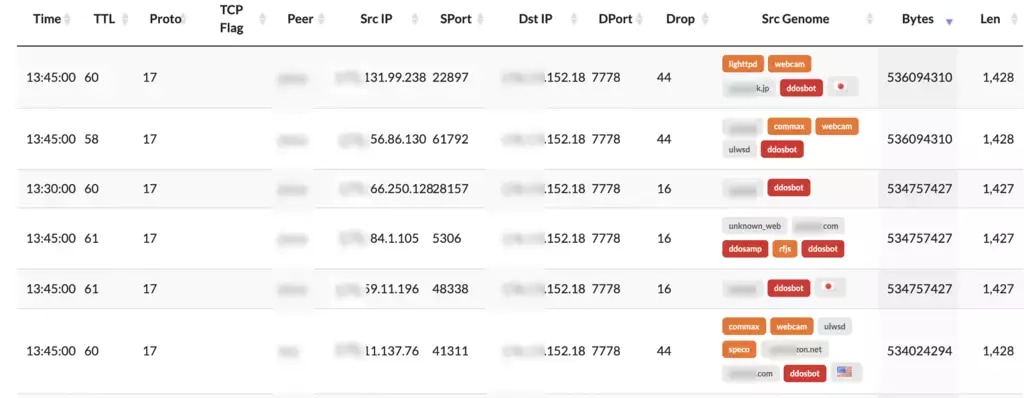
Figure 3: Deepfield Secure Genome tracking botnets in a specific hosting provider
An example of a botnet DDoS detection
Using knowledge of past DDoS attacks (from our Deepfield DDoS Library), our real-time “Internet security map” (Deepfield Secure Genome) and advanced ML algorithms can detect botnet DDoS with unrivaled accuracy.
For example, the figure below shows how our Secure Genome has identified 185.51.39.51 as a Hikvision Model 7513 PPOE camera. Instead of solely looking at the headers/payload (i.e., the “symptom” discussed earlier), our ML looks for patterns in the type and model of devices sending traffic.
So, for example, while one IP camera sending unsolicited traffic to a game server is unusual, seeing a large number of IP cameras sending UDP packets (to related destination IPs) is a strong indicator of DDoS traffic.
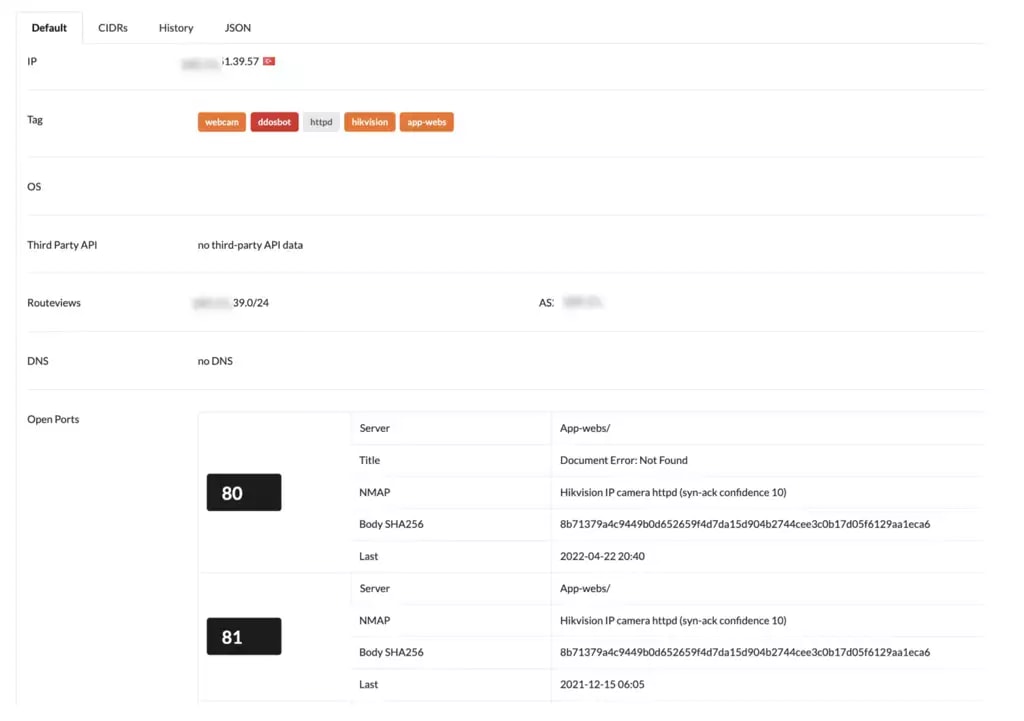
Figure 4: Deepfield Secure Genome identifies 185.51.39.57 as Hikvision model 7513
What about application DDoS?
As noted earlier, application DDoS today is almost exclusively a botnet problem. Instead of using synthetic traffic, most application-level DDoS focuses on generating high workloads using valid queries. Typically, the only distinguishing characteristic of application DDoS is that the traffic originates from botnets. So, the ability to detect application-level DDoS is largely dependent on the ability to detect DDoS botnets.
In our next blog post, we will explore the topic of DDoS mitigation and how to measure the efficiency of overall DDoS protection. Stay tuned.
If you would like to learn more about the challenges with DDoS detection (and botnet DDoS detection in particular), and how the latest generations of big data analytics, AI and MPl technologies can help, please join our LinkedInLive webinar, “Breaking Good: How to fight DDoS in 2022 (and win)” on November 10 at 11:00 am ET. Register here: LinkedIn
Learn more:
NANOG82 (2021) presentation: Tracing DDoS End-to-End
Nokia Deepfield Network Intelligence Report: DDoS in 2021
Nokia Deepfield DDoS Solution
IP Network Security


