The hidden threat of banking malware

5G, multi-access edge computing and the work-from-home paradigm are bringing new complexities to today’s networks — along with an array of cyber threats including banking malware. With the vast majority of mobile subscribers using smartphones to shop and bank online, malware embedded in trojans is clearly a threat communications service providers (CSPs) need to face and fight back against.
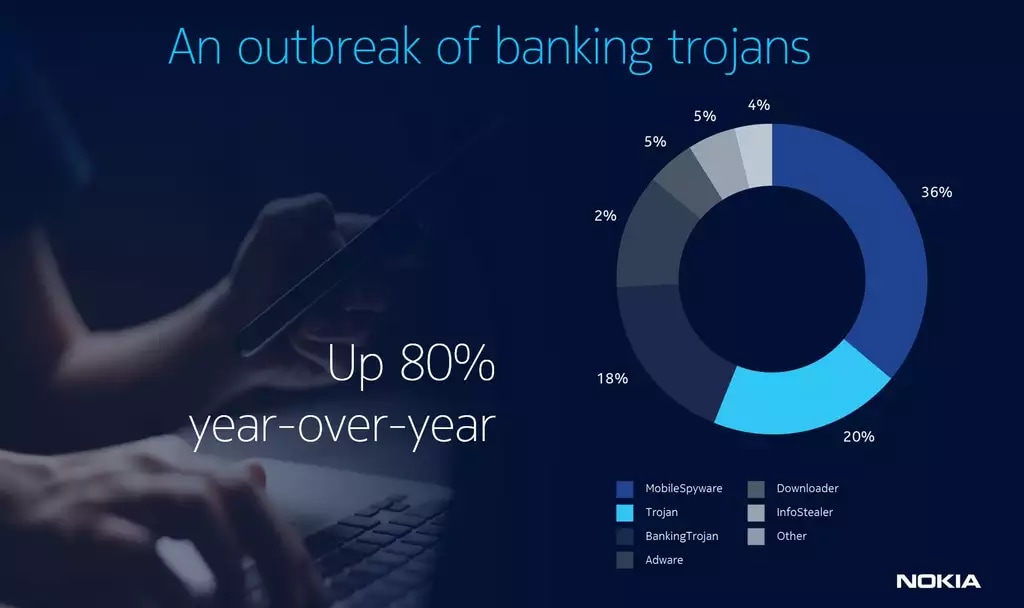
Banking trojans are typically designed to steal individual login credentials, banking details and credit card information. Their attacks on Android devices shot up 80 percent in 2021 compared to the previous year, according to Nokia data. Most of that activity was in Europe and Latin America — with FluBot, TeaBot, BlackRock, Cerberus, Mandrake and Banker.GXB prime culprits — but the risk is worldwide: 80 percent of the globe’s 5.2 billion unique mobile users use smartphones for online purchases, and in the U.S., 87 percent of Americans use their phones to check their bank balances.
How banking malware works
Banking malware has several ways of invading a smartphone. Most often, it will disguise itself as a friendly or frequently used app, requesting permissions to perform purported actions and then (often) disappearing from the phone’s application pane. In reality, it remains working in the background, collecting user information by capturing keystrokes and Google Authenticator codes, taking screenshots and superimposing overlays onto banking login webpages.
Once a banking trojan is on a phone, it’s hard to remove, which means CSPs’ best strategy is to prevent these malware infections from affecting their customers in the first place. A big part of that is helping subscribers protect themselves through education campaigns to best practices for cyber security.
Those practices include downloading apps only from official app stores, and by taking the following precautions:
- Setting strong passwords. Using password manager software and avoiding easy-to-guess passwords involving birthdays or pet names remain solid pieces of advice.
- Using multi-factor authentication. This requires hackers to have two different pieces of data to access individuals’ banking information.
- Avoiding public wi-fi. Subscribers should use only cellular data or trusted private wi-fi networks, since hackers can intercept information on public wi-fi.
A year of shifting trends
Beyond the spike in banking trojans, mobile security continued to evolve in other ways throughout 2021. In some cases, attacks declined: residential malware rates fell from their COVID-19 lockdown high, for example, partly because users upgraded their home networks and protections to support ongoing remote work.
Phishing attacks continued with a few seasonal peaks — spreading through email, social media and text messages, often posing as legitimate information about COVID-19 — and ransomware remained a threat, especially for overworked and overstressed healthcare networks and organizations. But, again, growing awareness of threats and improved security helped stem the tide.
A more dominant brand of cyber threat in 2021 was the supply chain attack, many of which grabbed headlines over the course of the year. First came SolarWinds: hackers used a software update mechanism to infect and access the networks of 18,000 customers, including U.S. government agencies. Next was Codecov, a corrupted bash script used by bad actors to capture network access credentials and tokens. And there was the infamous Colonial Pipeline attack, which cost the pipeline company a $4.4 million ransom and shut down its operations for days.
With more and more devices connected through the internet of things (IoT), more and more security vulnerabilities are being discovered and exploited. IoT device infection rates jumped by 100 percent between 2019 and 2020, and IoT botnet activity continued its steady climb — driven mostly by the Mozi botnet, which created individual botnets of up to 500,000 devices.
CSPs can take action
While threats continue to proliferate and evolve, and as networks continue to be more open — a necessity to seize 5G opportunities — there are many defensive strategies CSPs can employ to keep their networks and their customers safe.
One of the starting points is good information. Nokia’s 2021 Threat Intelligence Report provides valuable perspective on the current threat landscape based on aggregate data from networks protected by the Nokia NetGuard Endpoint Security solution, which monitors more traffic on more 200 million devices.
The report also factors in observations from ongoing analysis in Nokia’s lab and honeypot systems. Processing this information in our Threat Intelligence Center, which examines malware to help identify detection rules, allows us to create a comprehensive view of malware activity in fixed and mobile networks.
To read more about the latest security trends and tips, download and read the full 2021 Threat Intelligence Report here.
