XDR - Choosing the right solution for your modern security operations

Summary
- In the last year, XDR turned into a short-range technology that gained rapid adoption and acceptance in the market. Increasing focus on detection and response capabilities, combined with the limited availability and rising costs of skilled security practitioners, turned to a high level of adoption for XDR, with improved security outcomes.
- For a better understanding of the market and vendor positioning, industry analyst GigaOm recently assessed how well solutions for XDR are positioned to serve specific market segments. They investigated deployment models and took a key criteria comparison. Download the report to review their analysis of Nokia XDR Security solution.
- NOKIA XDR Security has been ranked as an outperformer – taking the leader vendor position of XDR solutions for the telecommunication service providers for both 4G and 5G communication service providers.
XDR gains rapid adoption and acceptance in the market
The XDR security solution is a value add-on with multiple use cases that can hunt for threats and investigate security threats while aggregating data. Last year I authored an article with helpnetsecurity on how security operations teams set up an average of 40 different point products across their networks and how most of these solutions are operating in isolation. By introducing strategies to move to an XDR solution, it’s clear that this technology is valuable at blocking threats in Security Operations Centers.

Now, we see that critical infrastructure providers such as telecommunication service providers can take advantage of adding response and threat detection capabilities to SaaS applications and cloud-based workloads to detect potential adversaries, malware or other network anomalies.
A key emerging technology is the public cloud adoption to implement new security technologies. This better caters to the protection requirements that many traditional security controls fail to match when it comes to securing cloud computing. This is done by having controls that offer the flexibility, scalability and access rights adequate to such environments.
Choose an XDR solution that increases SecOps efficiency
When I look to market trends these days, decision makers need to pay close attention to how XDR is shaping and influencing the security market. This is due to the sophistication of threat actors and their campaigns, and the expanded attack surface (e.g. 5G core network) which brings complexity to the security market. This complexity is driving an increasing need to introduce automation and advanced analytics as a core feature of many security technologies.
How can XDR use cases address key business objectives?
- They increase the need to triage alerts faster and with more confidence
- They identify and consolidate genuine security incidents
- XDR use cases show you how to quickly gather additional contextual data
- They take appropriate actions at speed
Low-maturity organizations are likely to leverage managed security operations center (SOC) services (managed security services or managed detection and response [MDR]) to deliver detection and response capacity. In this way, they would gain many of the benefits without the increased overhead that a lack of scale would create. More-mature organizations may still choose this route but have the additional option of integrating XDR technology into their existing security stack.
Invest in an XDR solution that maximizes existing security investments
While it can sometimes be difficult to know how much difference a security tool or platform is making, XDR delivers clear, measurable benefits. It helps reduce costs, increases efficiency and improves visibility across the entire cybersecurity estate. The latest XDR radar report by GigaOm 05/2022 allows you to view key criteria for enterprises and organizations, provides an overview of the XDR market, identifies capabilities (table stakes, key criteria, and emerging technology) and evaluation factors for selecting an XDR platform.
GigaOm’s statement on Nokia NetGuard XDR Security:
“Finally, we find that the solution is highly extensible with a wide range of connectors and integrations offered. Nokia’s solution is highly extensible and highly scalable. It has excellent network-level detection capabilities and strong case management and risk prioritization.
We found the solution to be very flexible. With integrations available for numerous mobile technologies and various cloud infrastructures, the variety of telemetry gathered will expand the solution’s effectiveness.”
Access the exclusive GigaOm Radar Report for Extended Detection and Response (XDR) Solutions.

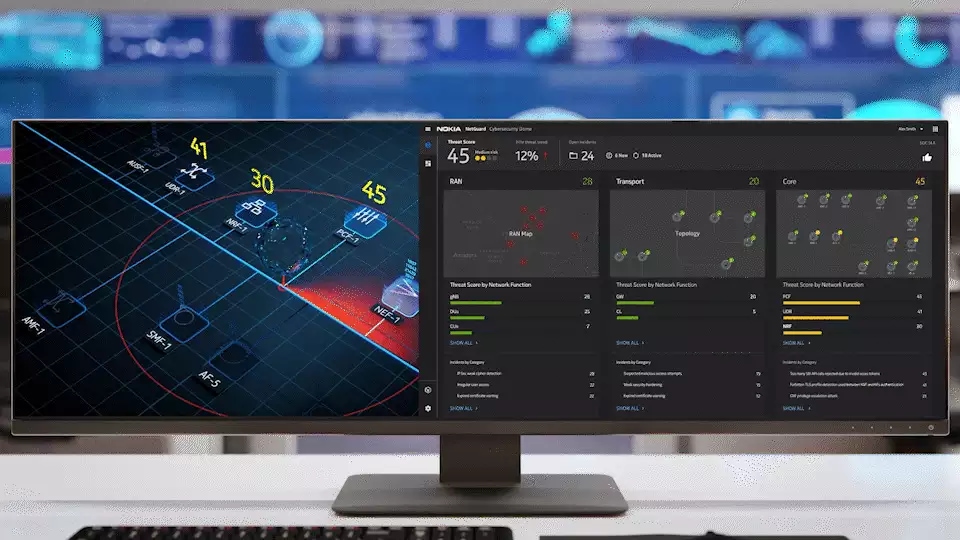
Nokia´s NetGuard Cybersecurity Dome, uses the combination of Nokia´s XDR security components to allow services providers to contain, analyze, and automatically remediate security incidents. It offers a set of pre-built 5G use cases for network security assurance.
The cloud-based SaaS allows security orchestrations teams to select use cases from a comprehensive catalogue to cover the entire telecommunication technology from the RAN to Transport and Core.
If you’d like to read more about Nokia XDR “NetGuard Cybersecurity Dome” to help you with XDR SaaS adoption, read the Powerful 5G Security Assurance Whitepaper.
To learn more about how the Cybersecurity Orchestration can help your organization achieve these goals, contact us for more information or request a free demo.



