Quantum-safe networks for power utilities, mining and oil and gas operations
Protect critical energy networks from present and future quantum cybersecurity threats
Bad actors are preparing to use quantum computing technologies to launch damaging cyber attacks on critical energy infrastructure. Secure your critical data and operations communications networks against present and future threats with Nokia quantum-safe networks for critical energy operations.
Why is the energy industry vulnerable to quantum threats?
Critical infrastructure has been a longstanding target for cyber criminals and the threat surface grows as we embrace digital technologies for operational improvements, safety, efficiency and more.
Modern energy companies—including power utilities, mining companies, and oil and gas operators—rely on the security and integrity of essential communications data transmitted across their networks. With continued digitalization, this data becomes an even bigger part of their industrial operations, it’s also a prime target for hackers, cyber criminals and other bad actors looking to disrupt critical services. Attacks and breaches are on the rise. The IEA reported in 2023 that attacks on European utility infrastructure doubled from 2020 to 2022, and in a report from CheckPoint Research, cyber attacks on U.S. power utilities rose 70% in 2024.
The energy industry currently relies on security solutions such as Transport Layer Security (TLS) to counter these threats. But the emergence of practical quantum computers capable of breaking common cryptography methods presents a new and bigger threat to energy companies: quantum attacks.
IEC 62351-9 recognizes that the quantum threat will put public-key algorithms at risk. These algorithms play a key role in current security solutions, including TLS.
So what does this mean for you? When bad actors get their hands on cryptographically relevant quantum computers (CRQCs), which have the potential to break current encryption protocols in minutes, they will be able to launch quantum attacks on your industrial infrastructure in two phases:
- Apply quantum algorithms to crack or hinder the encryption protection you use today and compromise your confidential industrial data.
- Use this data to gain an in-depth understanding of your operations and plan targeted man-in-the-middle (MITM) or denial-of-service (DoS) attacks on your infrastructure assets, such as power systems and pumps, compromising system integrity and operational safety.
Bad actors may already be preparing for this day, known as Q-Day, by eavesdropping on your communications and stealing your encrypted data as part of a harvest now, decrypt later (HNDL) strategy. They will hold on to this data so they can decrypt it later when a CRQC is available to render the encryption useless.
There is much to be concerned about in this scenario. But there is also good news: As you look to modernize your grid communications, we can help you make choices using existing technology to ensure quantum-safe energy communications, starting today.
A blueprint for quantum-safe energy communications
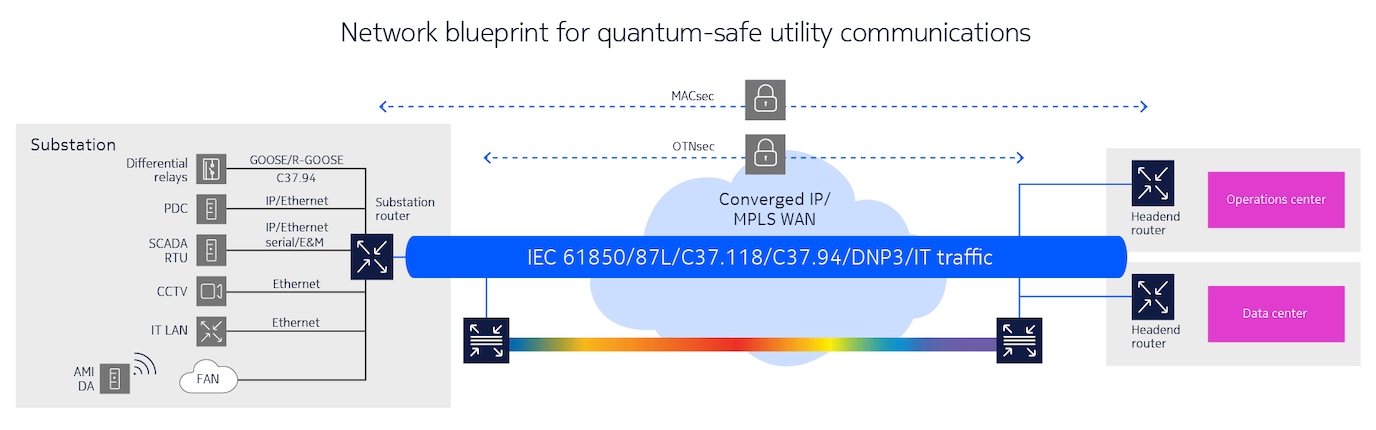
Our quantum-safe networking solution lets you protect your operational communications from current HNDL and future CRQC threats. It provides a multilayer, defense-in-depth security blueprint that uses quantum-safe encryption to turn your network into a strong first line of defense against any quantum attack.
Block quantum threats with strong, multilayer symmetric encryption
Robust encryption is a must for ensuring quantum-safe energy communications. Our outcome-based solution gives you the strongest possible quantum defense by harnessing the security strength provided by 256-bit symmetric key encryption across multiple network layers. This includes MACsec at the data link layer and OTNsec at the optical layer.
These technologies use AES-256, which can’t be cracked or overwhelmed by quantum algorithms and computers. They will protect your operations today and complement future standardized post-quantum cryptography (PQC) algorithms to provide an extra layer of protection.
Support quantum-safe algorithms with encryption key management
There are three different ways to distribute and manage quantum-safe encryption keys:
- Symmetric centralized key distribution (SCKD) sends decryption keys separately from encrypted data, making it harder for threat actors to get both pieces and access the data.
- Quantum keys, transmitted through a quantum key distribution (QKD) network, use the physical properties of photons rather than math problems to safeguard the key, making it possible to detect any third party that tries to intercept the key. This approach adds a layer of security against quantum hacking.
- Public-key cryptography (PKC) algorithms, the first set of which became NIST standards in 2024, will evolve public key infrastructures (PKIs) as they are adopted by security solutions and implementations become available.
A quantum-safe ecosystem will include all three of these approaches, matched with the appropriate network encryption, as well as other technologies as the quantum landscape evolves.
With our quantum-safe energy communications, you can select the key management approach that best aligns with your operational needs, existing infrastructure and security requirements. This flexibility enables you to implement quantum-safe networking while balancing effectiveness, practicality and resource allocation.
Stop fiber tapping with intrusion detection
Fiber tapping is the first step in a quantum attack in which bad actors try to harvest your data as it’s being transported through the network. Our solution provides optical intrusion detection tools that let you catch them in the act, including the Nokia Wavelength Tracker and optical Time-Domain Reflectometer (OTDR) capabilities. With these tools, you can detect and pinpoint intrusions to stop bad actors from accessing your data, eavesdropping on your communications and succeeding with HNDL schemes.
Get scalable, flexible, future-proof protection against quantum threats
We designed our solution to provide a scalable and flexible quantum cybersecurity solution that will protect your network against present, future and potential quantum threats. Our solution will integrate seamlessly with your current environment and support all your critical applications.
Our approach ensures that your communications remain quantum-safe in every part of your network infrastructure, from the core to the edge, and from field assets to data and control centers. You can adapt it as needed to ensure that you have the right level of encryption at every network layer—optical, Ethernet, MPLS and IP.
Why choose Nokia quantum-safe networks for energy and utilities?
Make energy communications quantum-safe today
Protect your sensitive communications now with a multilayer, defense-in-depth approach built around symmetric key encryption and random, high-entropy key generation. Add optical intrusion detection, firewalls, access control lists and network segmentation as needed to complete your quantum-safe energy communications framework.
Adapt your quantum cybersecurity defense to your business and use cases
Use the flexibility of our solution to deploy quantum-resistant encryption exactly where you need it. By layering encryption technologies such as MACsec and OTNsec, you can secure the data applications that matter to your business against any quantum threat.
Scale your defense as the quantum threat grows
Take the journey to quantum-safe energy communications at your own pace. Our solution lets you start small, adding the right encryption technologies to the most vulnerable spots in your network. As the quantum threat grows and becomes clearer, you can add more layers to expand and strengthen your defense.
Evolve your approach in step with the quantum landscape
Don’t wait for Q-Day or for international organizations to standardize new PQC algorithms. Use our solution to support quantum-safe energy communications and data today. Then seamlessly integrate standardized PQC algorithms when they’re ready. This will ensure that you’re ready for HNDL and for anything that happens after Q-Day.
Related industries
Related products and solutions
Solution
Protect your network with multi-layered embedded IP network security.
Solution
Keep mission-critical grid communications safe from cyber threats
Solution
Protect data from intrusion and theft through quantum-safe encryption, key management and intrusion detection
Learn more about quantum-safe networks for energy and utilities

Webinar

Article

Article

External news

Article

White paper
Podcast
Securing the future with quantum-safe networks for utilities – Part 1
Podcast