IP network security
Protect your AI and digitization ambitions with multilayered IP network security
Networks and data have never been at greater risk. As organizations embrace artificial intelligence (AI) and continued digitalization, they need new IP network security solutions that can stop increasingly sophisticated security threats that are targeting their networks and data in more ways and more places.
Nokia is addressing this need with a multilayered approach to IP network security. Our approach enables you to build scalable, secure and trusted networks that can help you manage risk and mitigate attacks before they impact business continuity.
Nokia Threat Intelligence Report 2024
Discover emerging cybersecurity trends and technologies and their impact on the telecom industry.

Why is IP network security critical?
The world is going digital, and petabyte volumes of data traffic now flow across public, private and corporate networks. As organizations apply technologies like artificial intelligence (AI), cloud, 5G, and quantum computing, IP networks will need to handle even more data.
Technologies such as quantum computing and AI will help unlock the next great innovations. But they will also give threat actors new ways to attack our networks and data. We’re already seeing this with AI-powered distributed denial-of-service (DDoS) botnets, emerging quantum computing threats, intricate data breaches and man-in-the-middle attacks.
Like organizations in every industry, you must prioritize security as you design IP networks for the quantum and AI era. But current security approaches don’t offer the scale or functionality you need to tackle bigger, more complex, and more frequent threats.
It’s time for an evolving approach to IP network security so you can protect your AI and digitalization ambitions.
Reap the rewards of a multilayered approach to IP network security
Network security must be a top priority in today’s evolving digital, AI and quantum world. But you need to do more than protect your networks and data. You also need to prioritize security as you deploy and support the network systems that make up the network. Nokia IP networks address these needs with an embedded security approach that provides:
1) Scalable and efficient protection provided for network systems, customers, and data.
2) IP trusted systems with system security and trust, with a secure lifecycle to deliver security at scale.
3) Quantum-safe IP communications are delivered securely at network scale with high service performance.
4) Automated, AI-driven DDoS protection that stops the biggest threats
Why choose Nokia for IP network security?
We help you achieve the comprehensive security protection you need by embedding security into layers of the IP network.
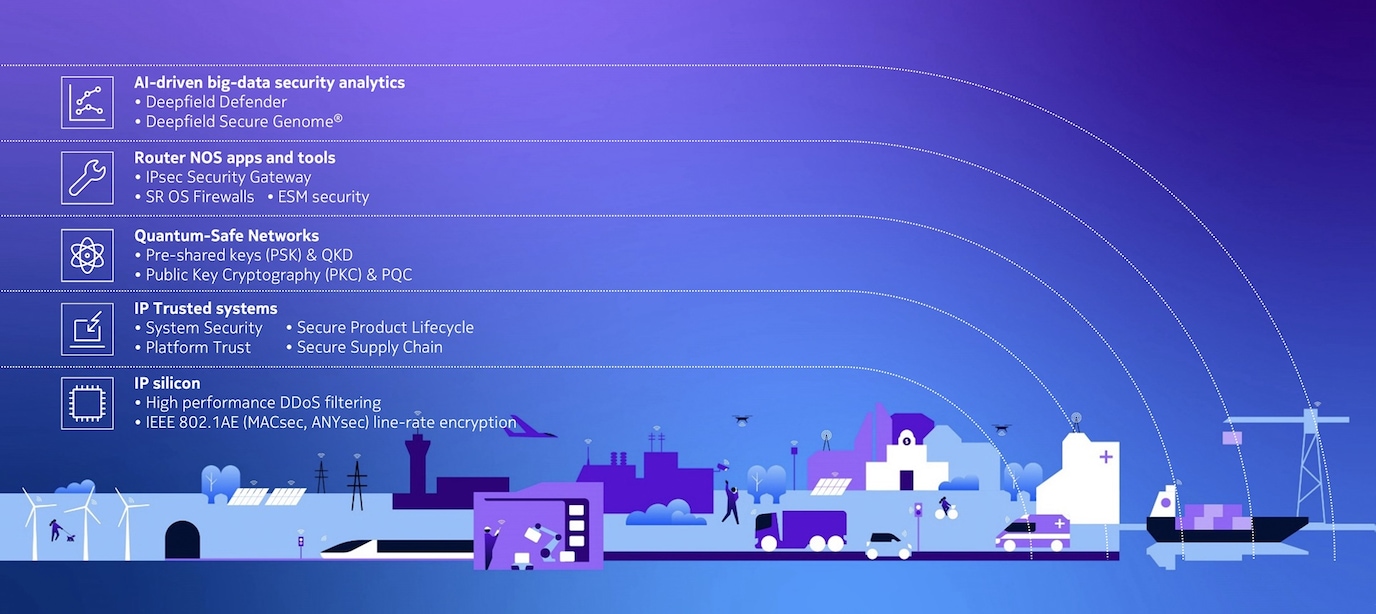
Protect your AI and digitization ambitions with multilayered IP network security
Our approach empowers you too:
Shield your customers and services against the latest generation of DDoS attacks
Harness the power of big data analytics and AI with Nokia’s cutting-edge solution to detect and neutralize all DDoS attacks—botnet-based, hyper-volumetric, and application layer—in seconds. Achieve unmatched scale, efficiency, and cost-effectiveness in your fight against cyber threats.
Transform your DDoS security into a revenue stream by offering next-generation DDoS protection as a service, unlocking unparalleled opportunities for growth and innovation.
Our DDoS solution combines:
- Deepfield Defender, a petabyte-scale, AI-driven DDoS security and analytics platform.
- Deepfield Secure Genome®, a Nokia-patented cloud-based data feed that continuously tracks the security context of the whole internet.
- Programmable FP silicon embedded into our IP routers and next-generation 7750 Defender Mitigation System.
Fortify against quantum threats with quantum-safe IP networks
Fortify your network defenses against quantum-enabled threats with our proven IP Quantum-Safe Networks. Deploy today for robust IP cryptography (MACsec, ANYsec, IPsec), powered by quantum-safe key entropy, strength, and distribution, all secured with AES-256 network encryption for unmatched protection.
To achieve a quantum-safe outcome today, you can apply our IP cryptography across a single network layer—or, if required, two or more network layers—to meet your business and application requirements.
Empower your communications with our Quantum-Safe Networks, engineered for crypto-agility, crypto-resiliency, and advanced quantum-safe cryptography. Safeguard against today’s and tomorrow’s quantum threats while delivering unparalleled network scale and service performance.
Strengthen your protection with robust security applications and tools
Elevate your network’s defenses with a robust suite of router applications and tools, including:
- A modular, carrier-grade router-based IPsec Security Gateway that delivers scalable throughput and flexible resiliency to deliver industry-leading performance.
- Integrated firewalls that perform stateful, in-line packet inspection to stop unsolicited traffic from breaching the secure zones of the network.
- Enhanced subscriber management capabilities that stop attackers from impersonating valid users or subscribers.
Engineered for scale and resilience, our solutions deliver robust protection against evolving threats, ensuring your infrastructure remains secure, scalable, and high-performing to meet the demands of a digital world.
Secure your future with IP trusted systems
Secure your digital landscape with our IP trusted systems, engineered to deliver uncompromising security and trust against platform-level threats. Our robust design safeguards management and control planes, blocking unauthorized access, securing routing, and neutralizing traffic flooding attacks with precision.
Our platform trust uses advanced system integrity verification and encryption, including secure and measured boot alongside Trusted Computing Group (TCG)-compliant TPM 2.0 Keys for reinforced device identity and attestation.
Our commitment to security extends through a secure product lifecycle, blending proactive and reactive measures with a Design for Security (DFSEC) approach. Supported by a fortified hardware and software supply chain, we implement a continuous strategy of prevention, detection, and response, ensuring protection across every partnership and touchpoint.
Our IP trusted systems empower your future with singular security and reliability.
Achieve unmatched security and performance with advanced IP silicon
Our multilayer approach is underpinned with high-performance security features built into our FP silicon to keep your network secure without impacting its performance. These include:
- Integrated line-rate network encryption to protect network connectivity at capacity and scale.
- Precise, highly scalable attack filtering capabilities that support hundreds of thousands of access control list (ACL) filters.
- High forwarding capacity and enhanced packet intelligence and control, to ease DDoS attack mitigation.
Safeguard your infrastructure without compromising speed or efficiency, ensuring robust protection for evolving digital demands.
With our approach, you have the tools you need to identify and mitigate current or future threats, from botnet DDoS to quantum-enabled cyberattacks while securing your network systems, customers and data.
Explore topics related to IP network security

Quantum-safe networks
Making critical infrastructure quantum-safe.

DDoS security
Defend your network against botnets and application-layer attacks with an AI-driven DDoS security for fast and accurate detection and real-time mitigation

Cybersecurity
Industry leading end-to-end 5G security.
Discover our IP network security products and solutions
Product
A next-generation platform for DDoS mitigation
Product
High-performance IP edge and core routers
Product
Next-gen, big data and AI-driven DDoS detection and mitigation solution
Product
Keep your customers’ IP traffic quantum-safe in the quantum era
Product
Highly flexible IP edge router designed for cloud environments
Learn more about IP network security

Blog

Blog

Blog

Customer success

Topic

Blog

Blog

Application note
Latest news
Please complete the form below.
The form is loading, please wait...
Thank you. We have received your inquiry. Please continue browsing.
